2024鹏城杯
Web
ezlaravel-pcb2024
cve直接打
【漏洞复现】CVE-2021-3129_laravel
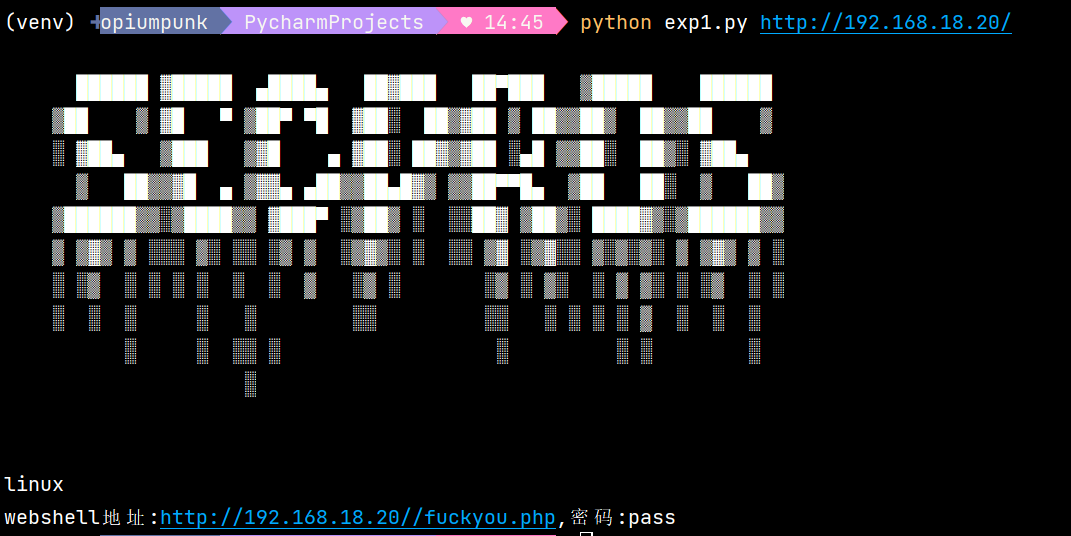
哥斯拉3之前连接
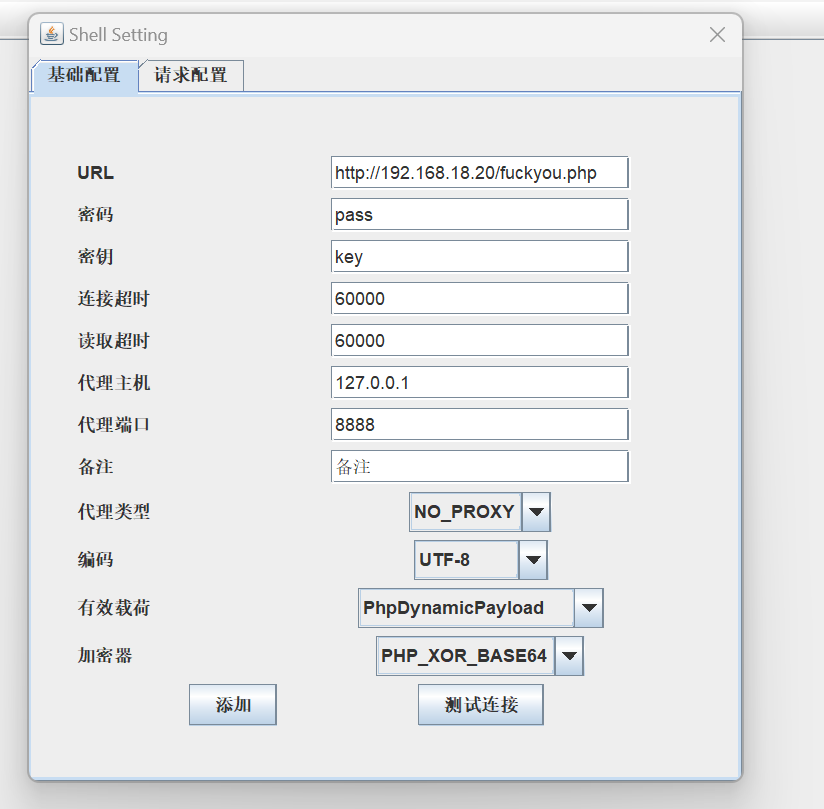
python口算
脚本:
import requests |
得到hint
|
脚本,ssti得到flag
import requests |
Misc
Simple_steganography
解压得,secret.zip有密码打不开,hint.txt给的是a=7,b=35
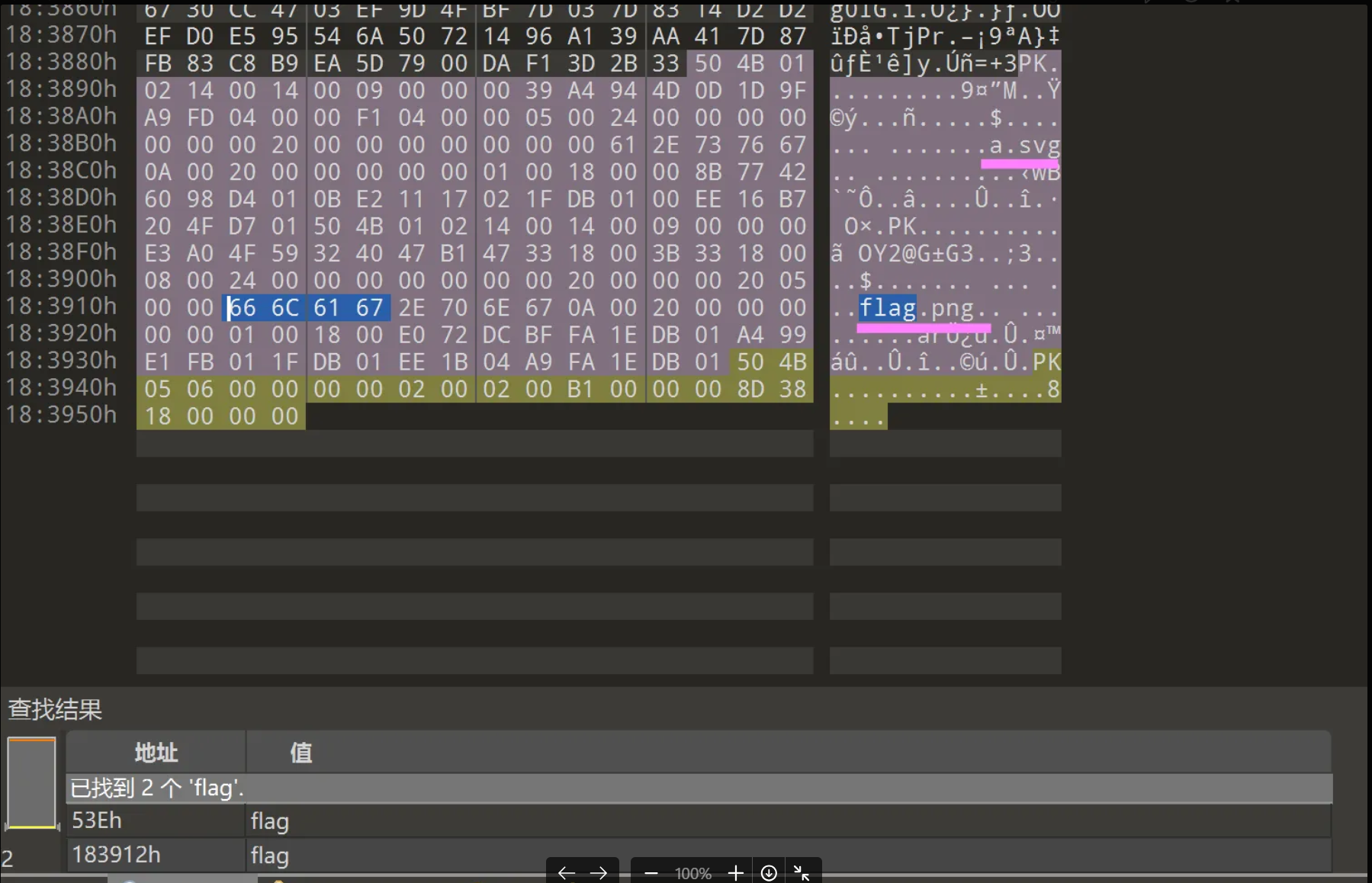
010打开secret.zip,发现里面还有东西,binwalk出不来,这时候我们需要用到明文攻击,工具:bkcrack
首先准备两个文件,pnghead和svghead:
pnghead https://github.com/hack3r0pium/hack3r0pium/blob/main/pcb/pnghead
svghead https://github.com/hack3r0pium/hack3r0pium/blob/main/pcb/svghead
然后使用命令得到密匙
bkcrack.exe-C secret.zip -c flag.png -p pnghead
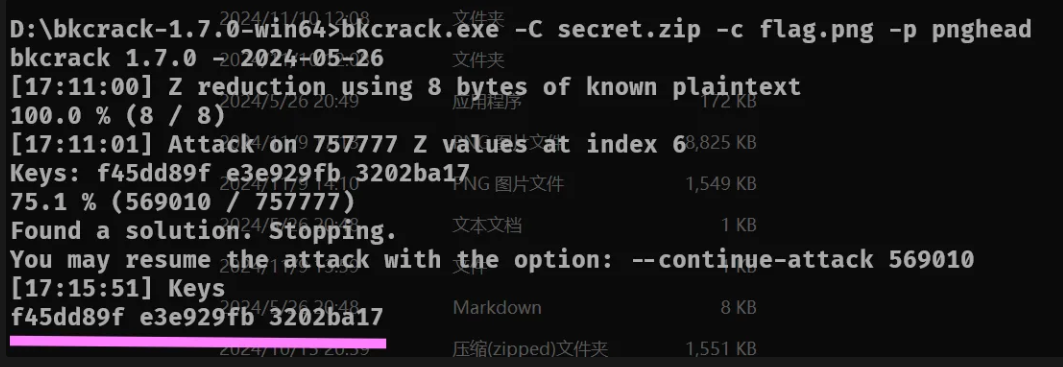
再使用命令得到flag.png:
flag.png

同理使用命令得到a.svg:
bkcrack.exe-C secret.zip -c a.svg -p svghead
bkcrack.exe -C secret.zip -c a.svg -k f45dd89f e3e929fb 3202ba17 -d a.svg
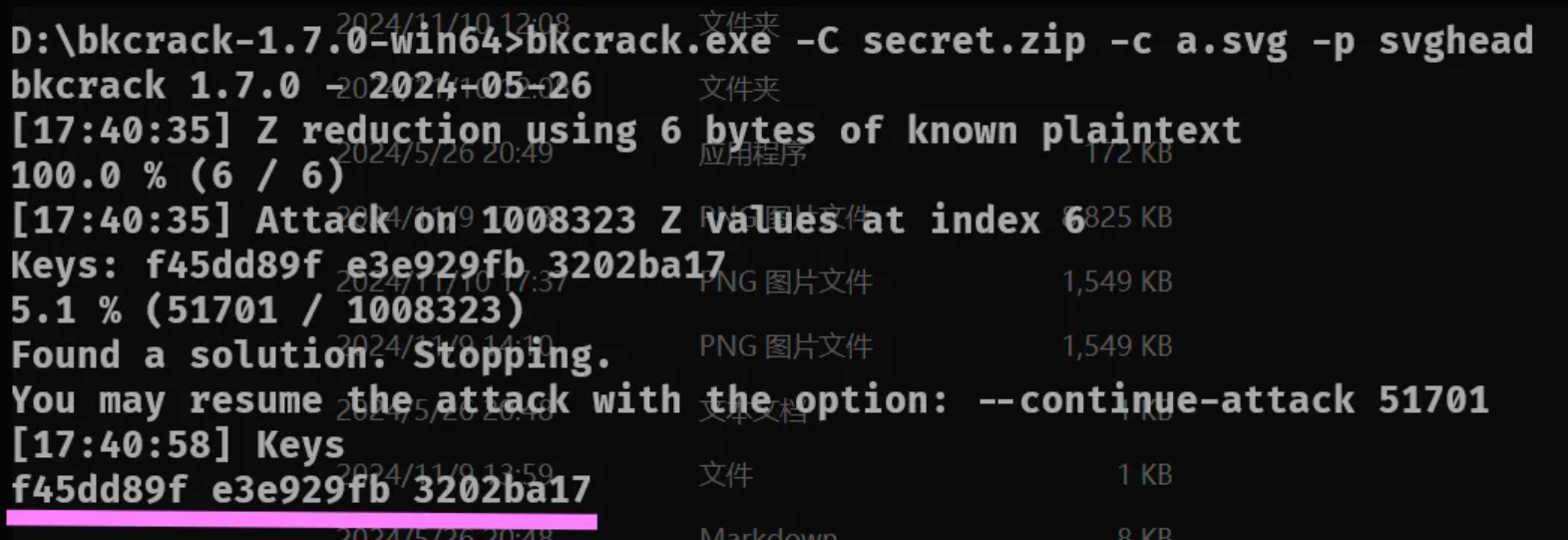
a.svg:
给出这个黄金分割率svg文件我至今都不知道有什么用,当时一直把hint给的a=7,b=35结合这个来想,结果浪费了一大堆时间……
先把得到的flag.png放进010,发现crc值不对,直接脚本爆破宽高
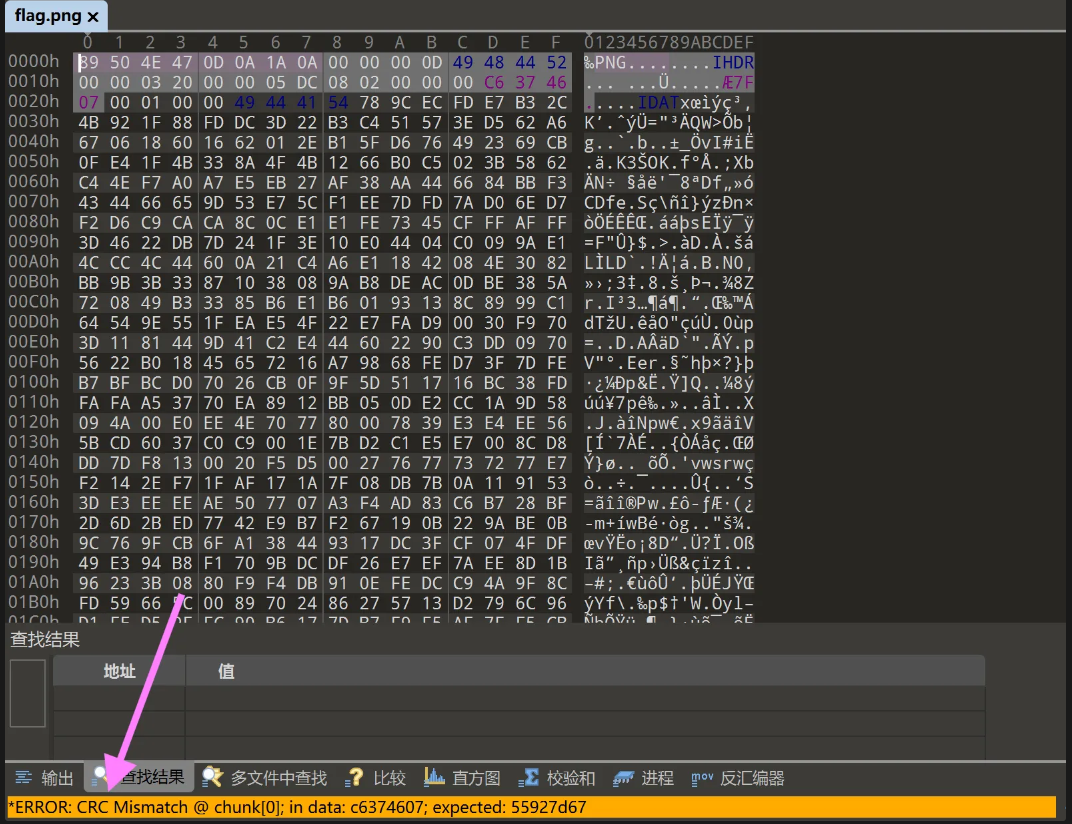
脚本:
import binascii |
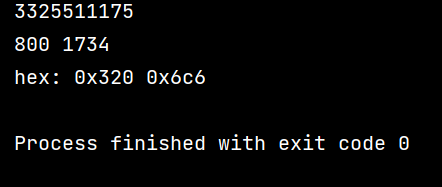
改好宽高得到一部分flag:

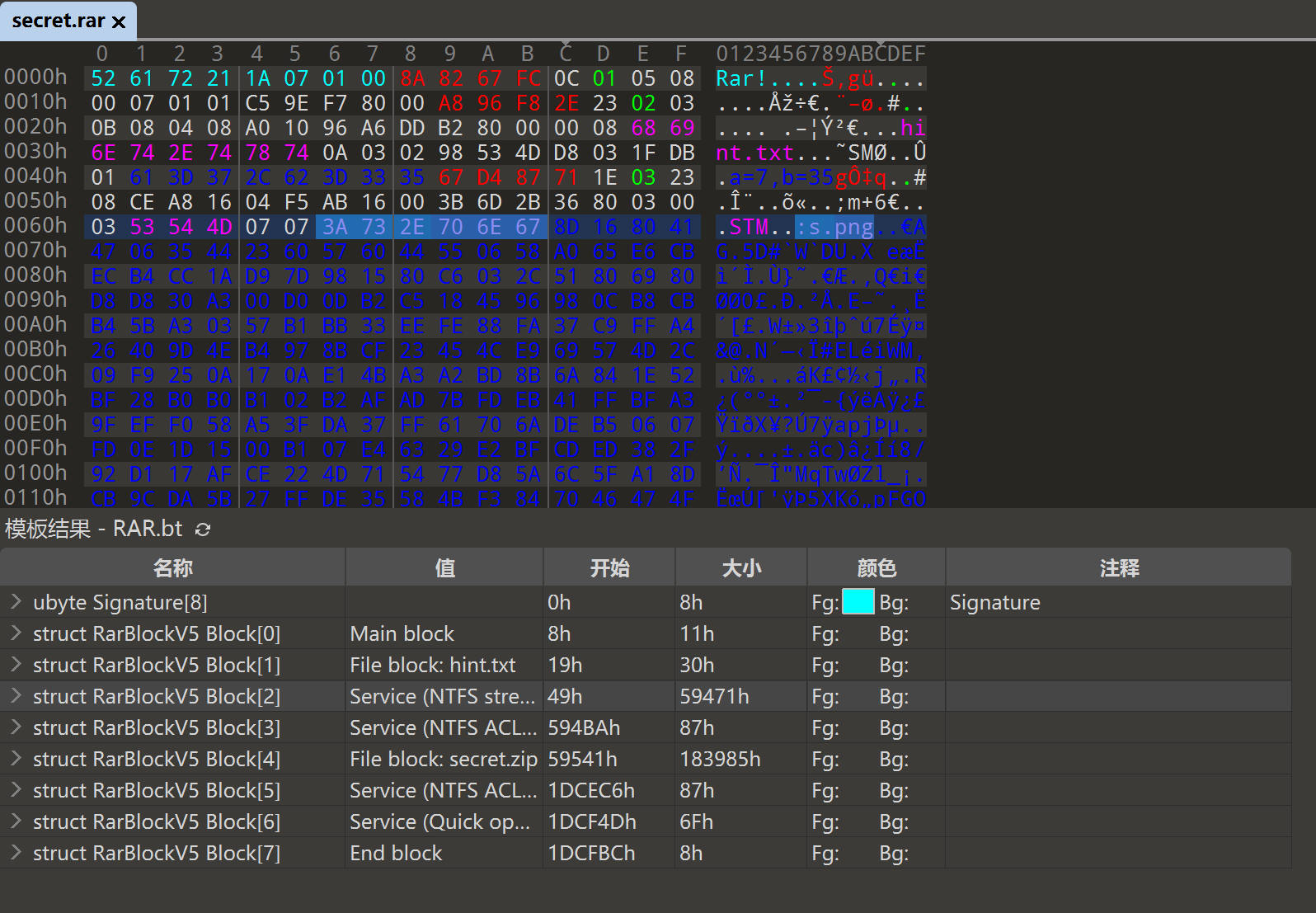
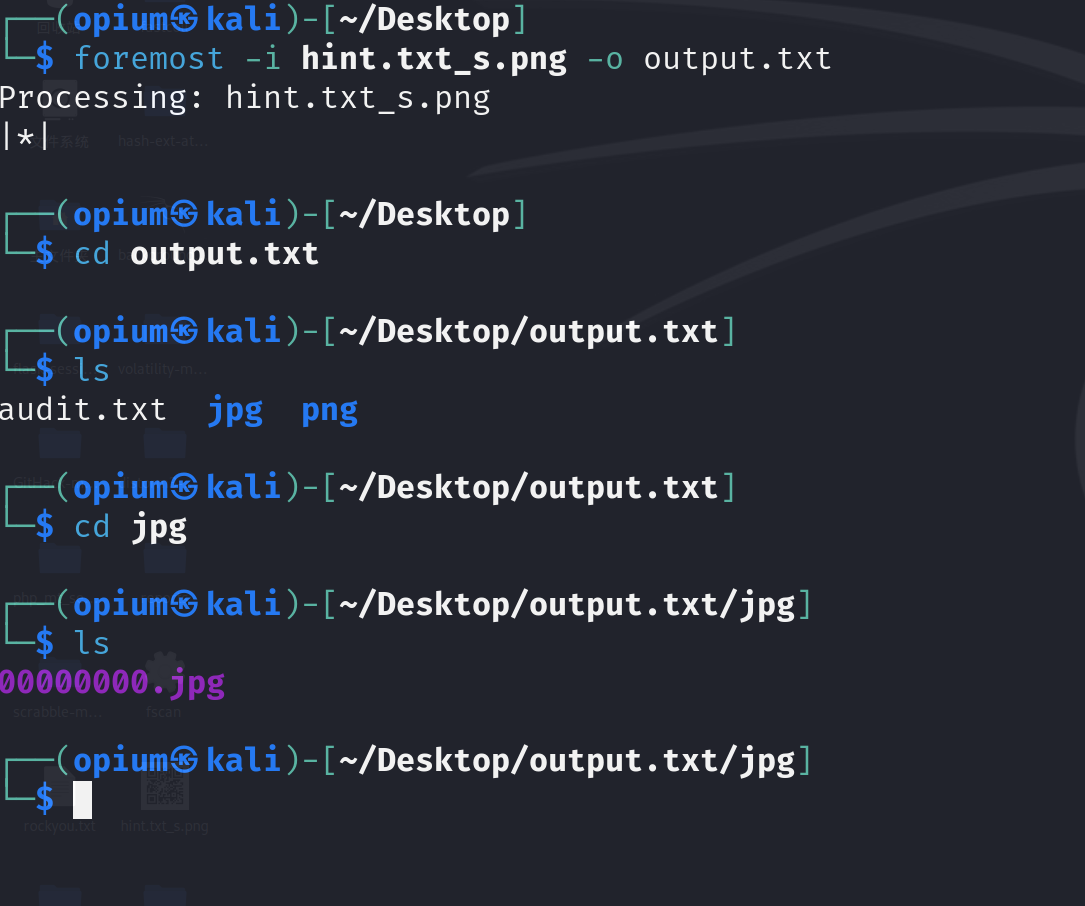
找到这个后我们需要找到s.png,这个隐藏的是真的深,要在原本的secret.rar找到,打开010,运行RAR模板,会发现有NFTS流
提取s.png的方法很简单,直接7z打开secret.rar然后就能找到s.png,复制出来就行,然后扫码发现是假flag

然后用010打开发现里面还有jpg,手动提出来或者foremost提出来就行
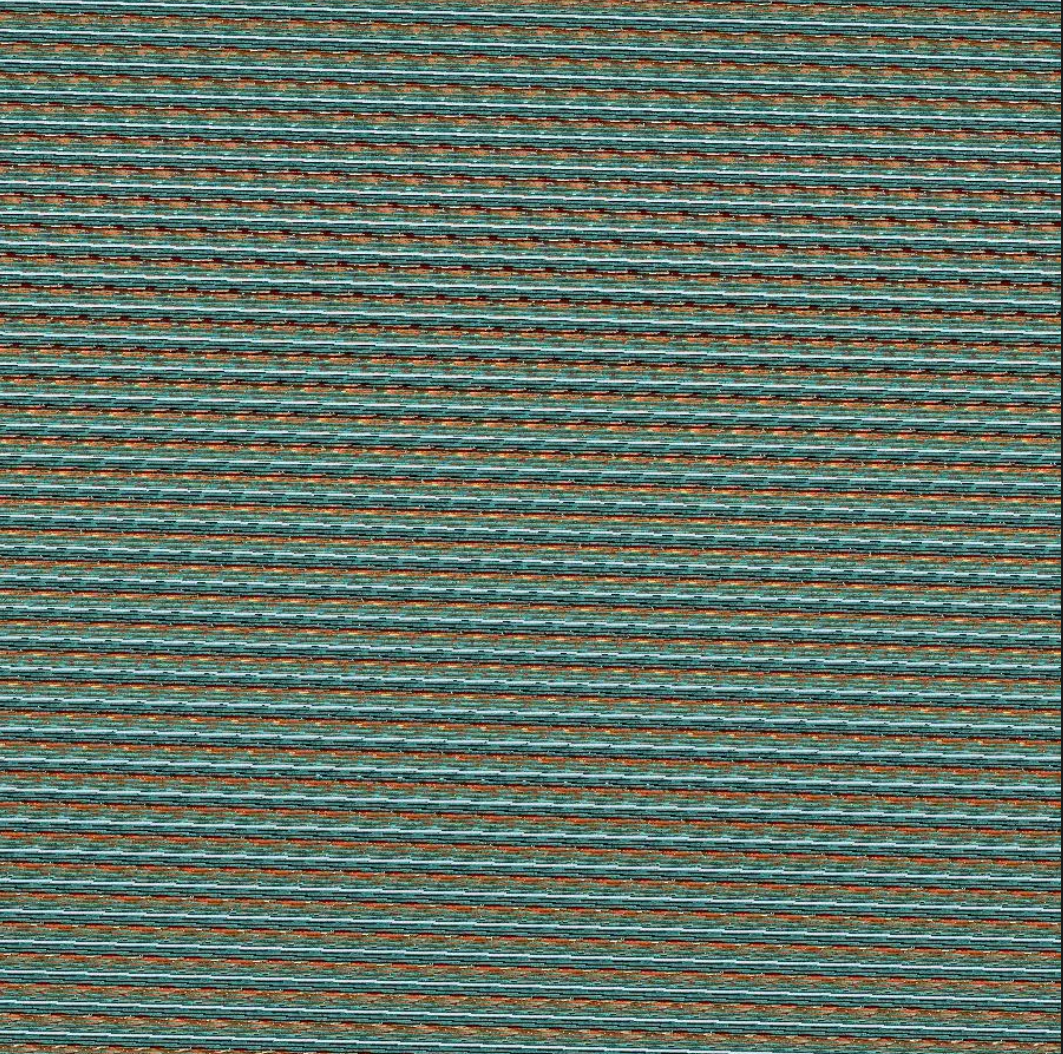
而这时候结合提示a=7,b=35可以想到猫脸变换arnold’s cat map
脚本得到flag另一部分图片:
import numpy as np |

本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 0pium's Blog!



